How Real-Time SMS Fraud Detection Works
Discover how CheckTxt analyzes suspicious SMS messages in real time and gives enterprises visibility into customer-targeted attacks beyond the security stack.
Clarity when it matters most.
CheckTxt fraud detection workflow
Real-time analysis and response pipeline for suspicious SMS messages
No app.
No login.
No installation.
• Scam and social language
• Brand impersonation indicators
• Malicious URLs and domains
• Sender behavior and anomalies
• Urgency, pressure, and trust-exploitation patterns
No technical jargon.
No false alarms.
Just clarity.
• Alerts to security teams
• Campaign-level visibility
• Active takedowns of malicious infrastructure
It's easy for customers and employees to use
No Apps. No onboarding.
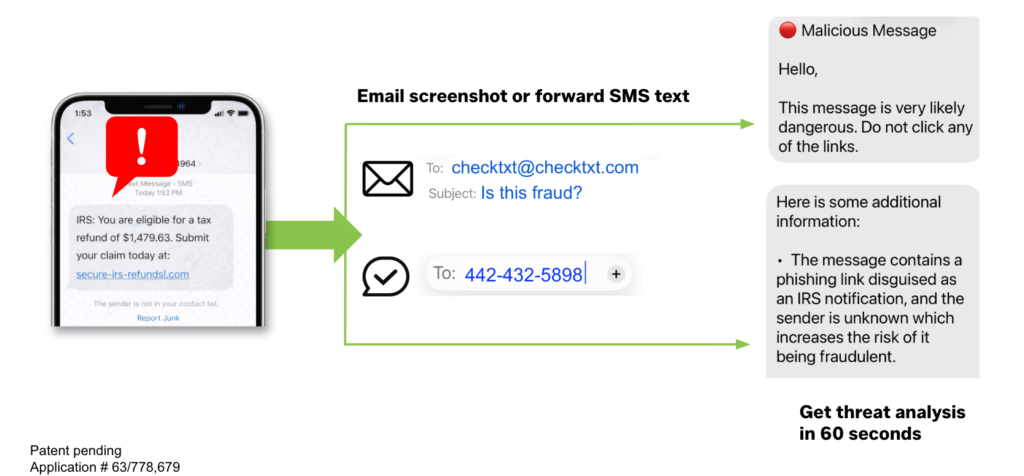
CheckTxt in action
This short demo shows how CheckTxt verifies suspicious text messages in under 60 seconds. Simply forward a message and receive a clear verdict—no app, no account, no setup required.
See how easy it is to check SMS scams and get instant clarity.
CheckTxt’s Compound AI Technology: Advanced Protection Made Simple
Patent-Pending CHAI Engine (USPTO 63778,679)
CheckTxt’s patent-pending CHAI engine analyzes suspicious text messages using multiple, specialized detection layers—working together to deliver a clear, accurate verdict in under 60 seconds.
Each layer focuses on a specific fraud signal. Together, they enable real-time SMS fraud and scam detection with zero false positives.
Message content & linguistic analysis
Analyzes SMS language for scam structures and social-engineering tactics such as urgency, authority, and payment requests.
Campaign & behavioral pattern detection
Detects repeatable patterns across messages to identify coordinated SMS scam campaigns and AI-generated variants.
URL & Domain Risk Assessment
Evaluates embedded links for malicious domains, redirects, and known fraud infrastructure before users click.
Real-time, multi-layered threat analysis
A compound AI architecture evaluates messaging fraud risk in real time. Content patterns, sender behavior, links, and impersonation indicators are synthesized to determine intent and detect emerging attacks.
Continuous model training & signal refinement
Continuously adapts to new scam techniques and fraud patterns without manual tuning or configuration.
Enterprise-grade Azure infrastructure
Delivers fast, reliable analysis on secure Microsoft Azure infrastructure with privacy-first controls.
Why Existing Security Controls Miss SMS Fraud
- No MDM required - Instant deployment without complex setup
- Personal device friendly - Protect BYOD without privacy invasion
- SMS-specific expertise - Purpose-built for text message threats

- Checktxt’s compound AI engine - demonstrates exceptional accuracy and consistently delivers high-quality results.
- Enterprise management - Centralized control and reporting
- Professional threat intelligence - Real-time analysis, not just blocking

- Direct protection - Actionable results, not just intelligence
- Immediate response - 60-second analysis vs. hours or days
- Proactive takedowns - We eliminate threats, not just report them

